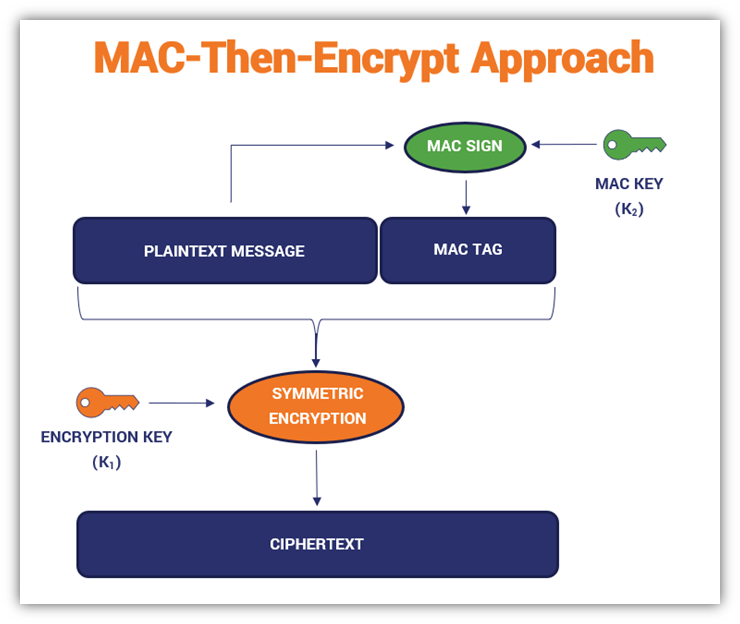
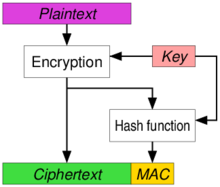
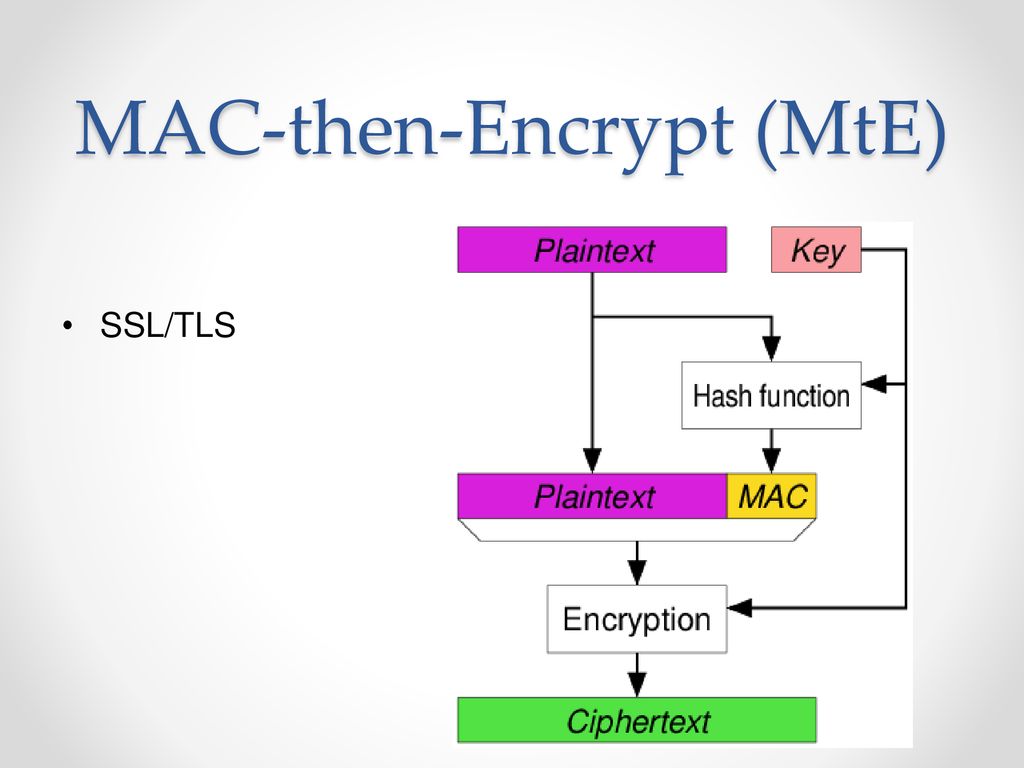
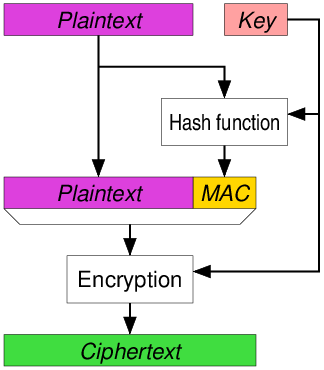
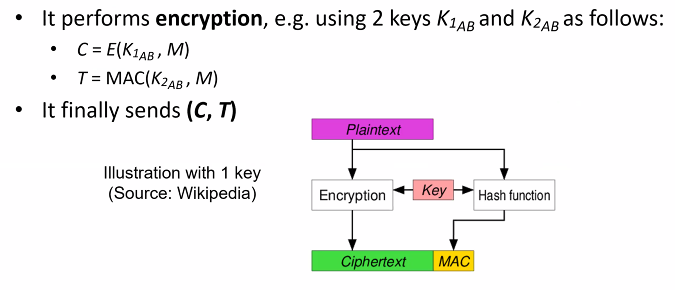
![PDF] Encrypt-then-MAC for Transport Layer Security (TLS) and Datagram Transport Layer Security (DTLS) | Semantic Scholar PDF] Encrypt-then-MAC for Transport Layer Security (TLS) and Datagram Transport Layer Security (DTLS) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1a5dfd4e044ab934e2a10d666d7951d23a3cb235/5-Table1-1.png)
PDF] Encrypt-then-MAC for Transport Layer Security (TLS) and Datagram Transport Layer Security (DTLS) | Semantic Scholar
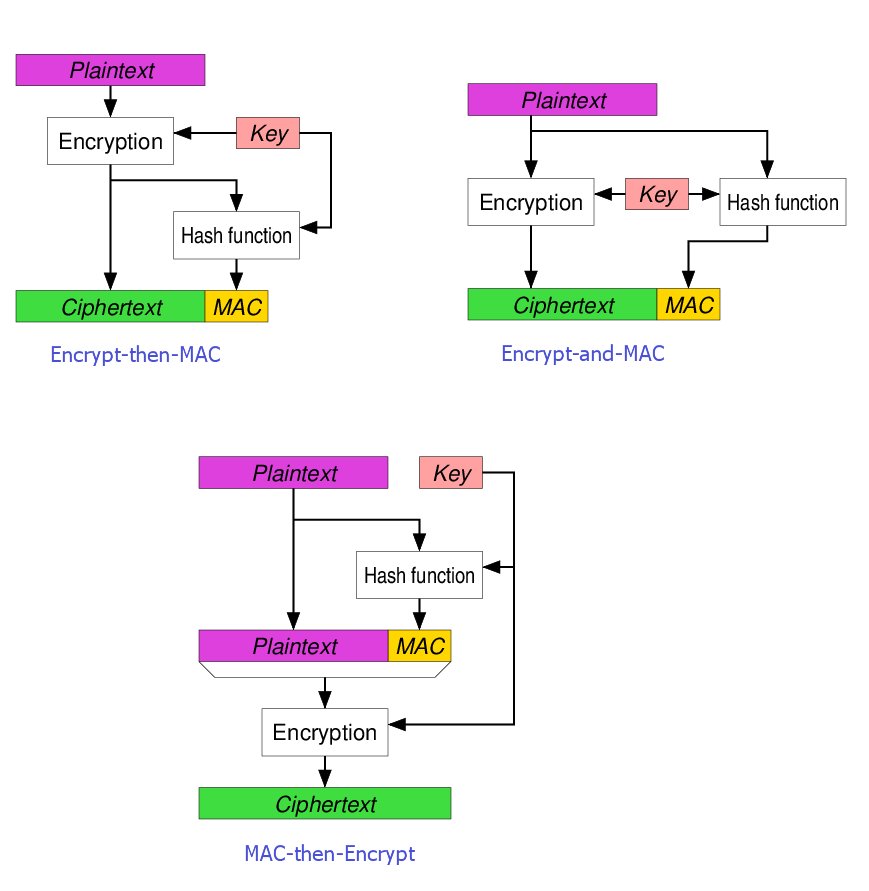
GK Palem on X: "Among the three methods for #Blockchain #Ciphers the Encrypt -Then-MAC has been regarded as the highest definition of security with "strongly unforgeable" MAC, compared with MAC-then-encrypt or Encrypt-and- MAC. Authenticated
GitHub - SoursosK/Encrypt-then-MAC: A demo app applying the Encrypt-then-MAC scheme to a phrase, using AES-CBC 256 and HmacSHA256.