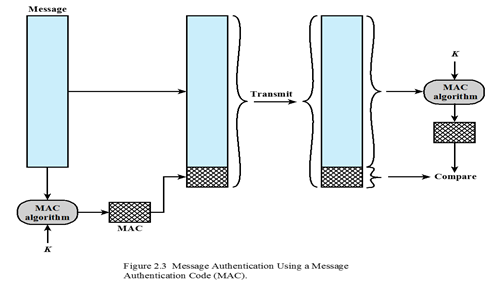
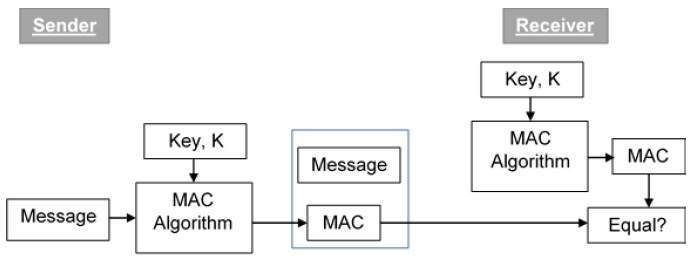
Architecture of the security module implementing the Encrypt-then-MAC... | Download Scientific Diagram
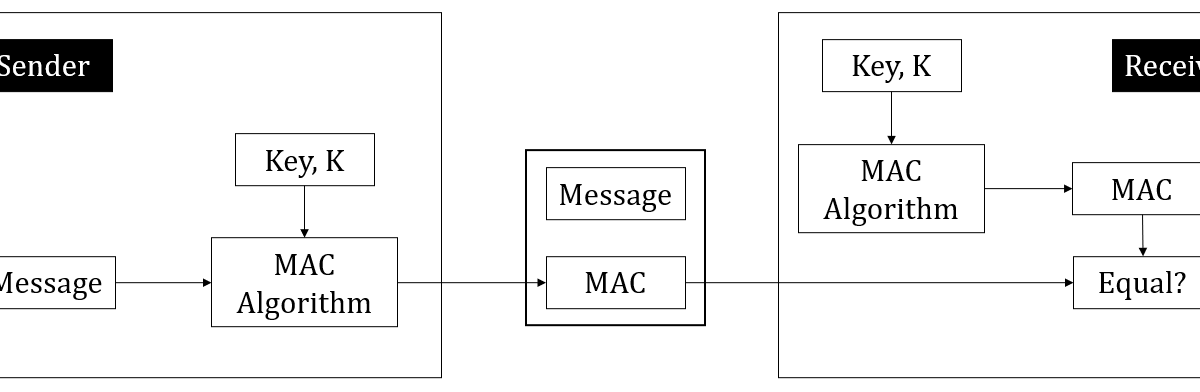
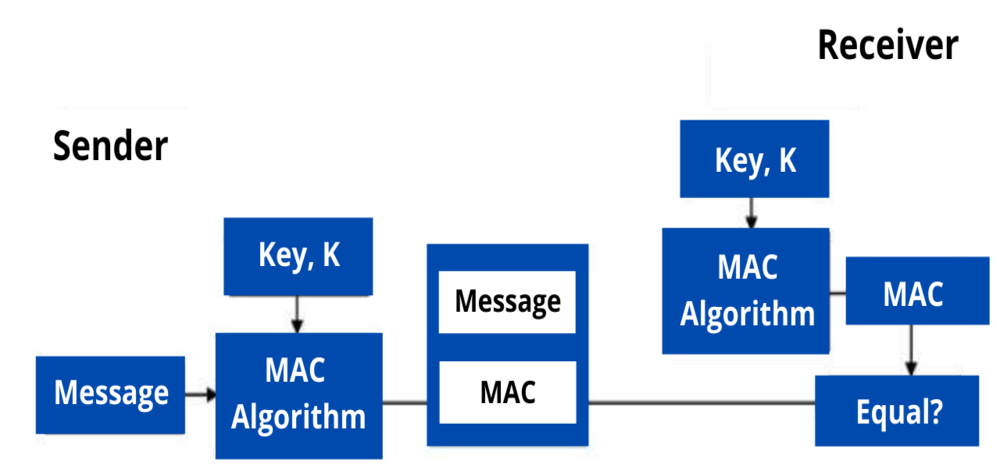
Chirag's Blog: Introduction of MAC (Mesage Authentication Code) | Application of Messsage authentication code | Importance of MAC

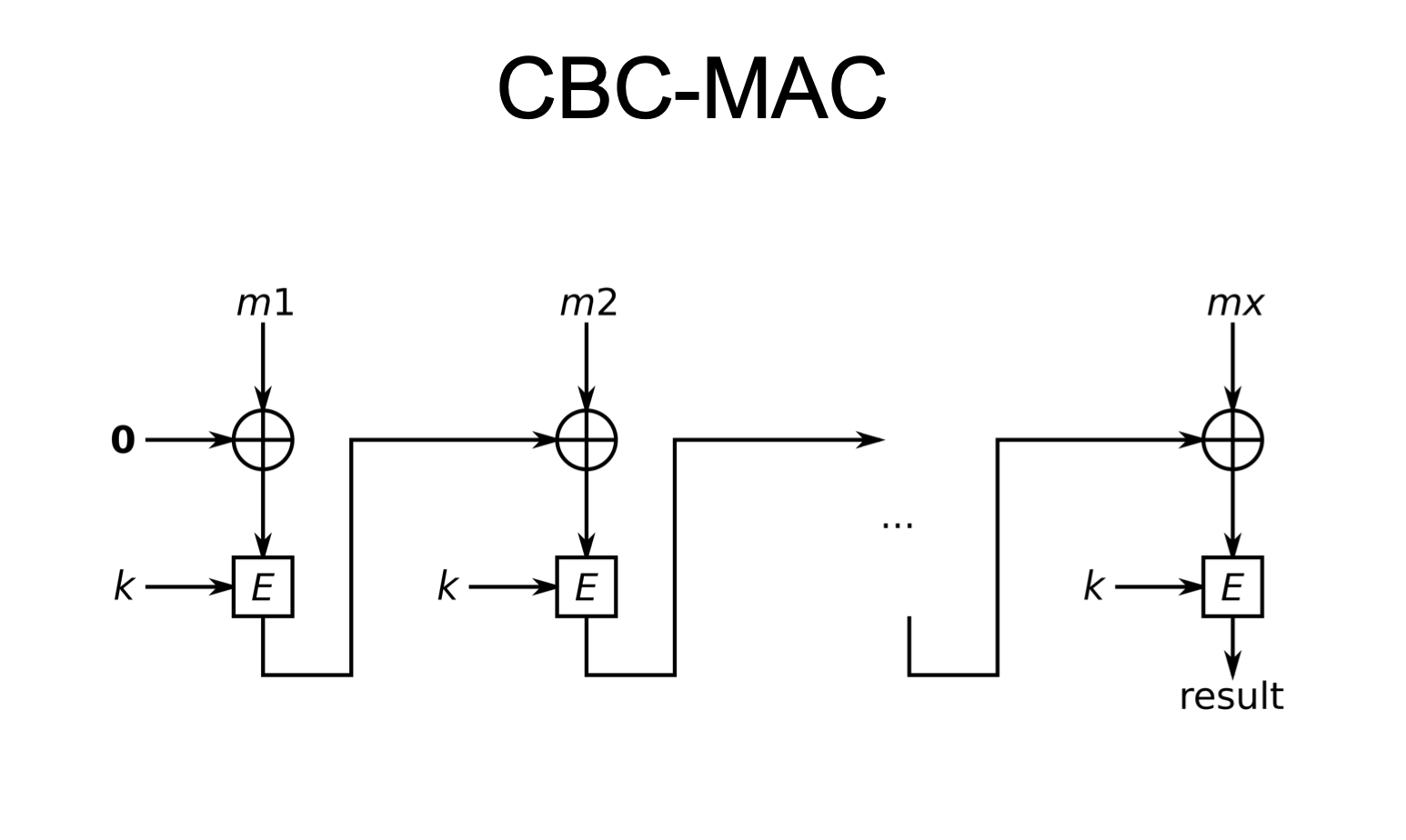
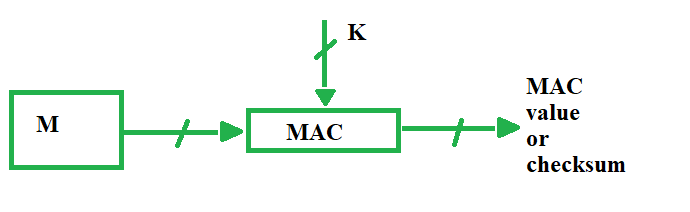
On the left, most MAC algorithms involve the key in the computation... | Download Scientific Diagram

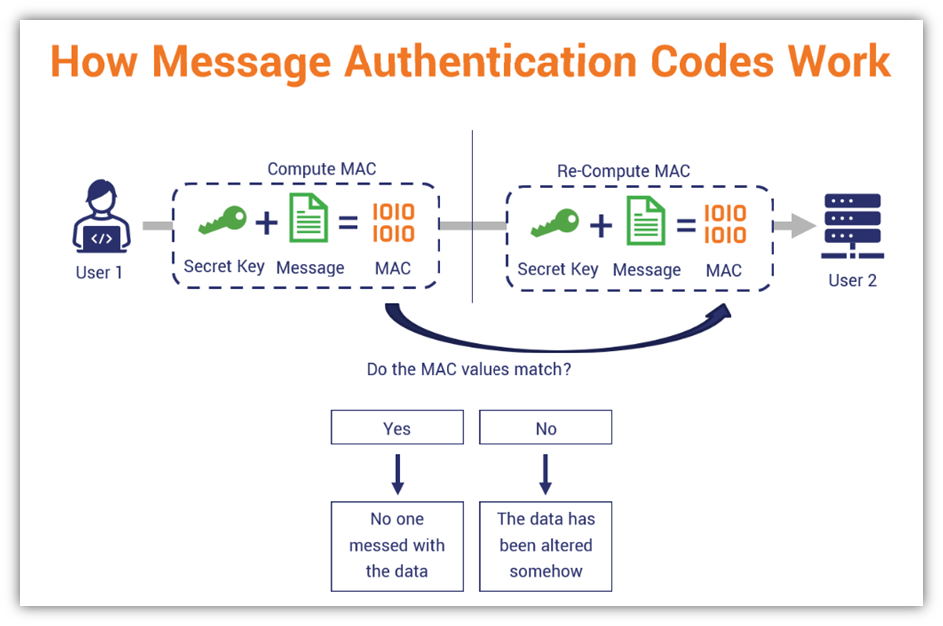
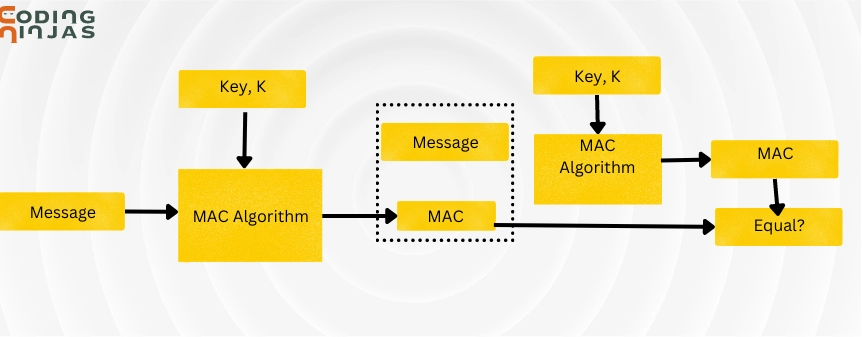
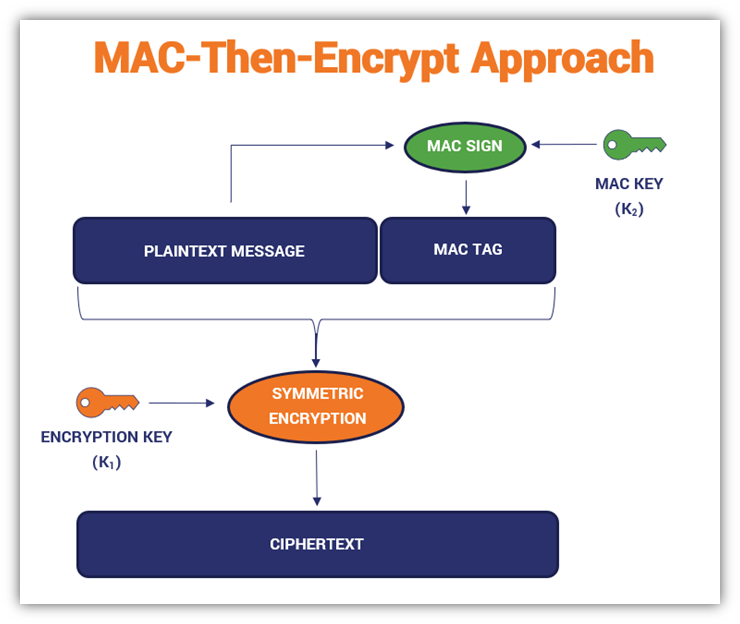
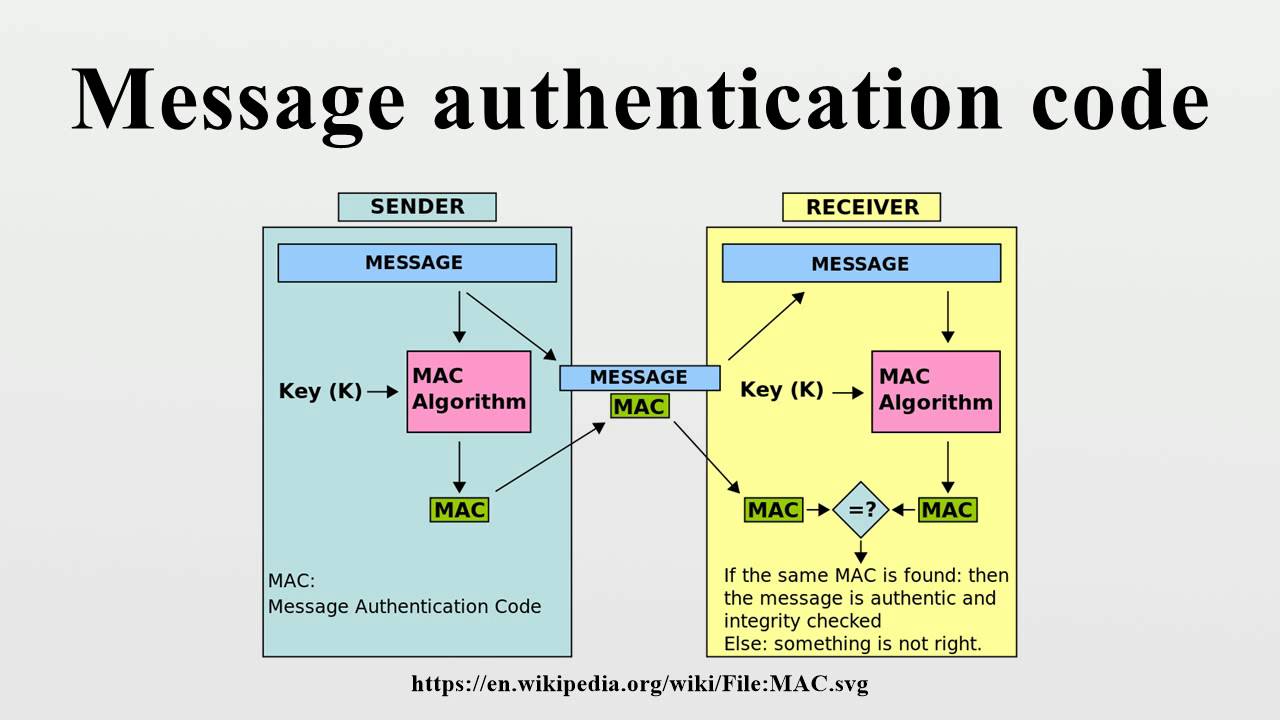


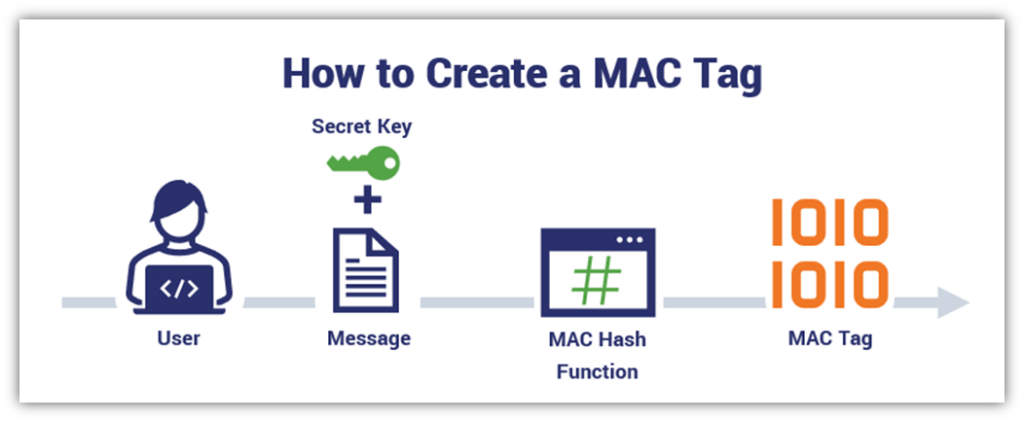
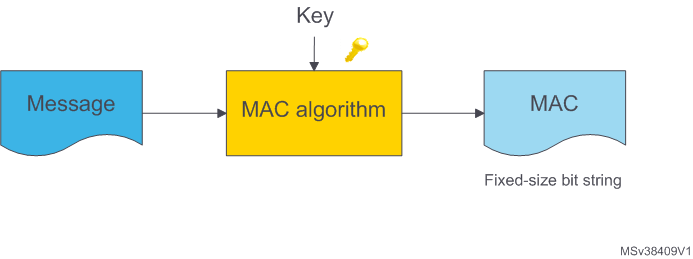
![PDF] Applying Message Authentication Code (MAC) in text chatting system | Semantic Scholar PDF] Applying Message Authentication Code (MAC) in text chatting system | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6b893ee5cd963b857d86aae215c6fc659978f523/4-Figure1-1.png)